[Note on Brand Evolution] This post discusses concepts and methodologies initially developed under the scientific rigor of Shaolin Data Science. All services and executive engagements are now delivered exclusively by Shaolin Data Services, ensuring strategic clarity and commercial application.
Cloud computing presents a compelling opportunity for a firm to reduce infrastructure overhead and offload significant operational risk. With services like Infrastructure as a Service (IaaS), a company can build a virtual presence while the service provider handles the physical infrastructure (Kirubakaran, 2020). Many firms choose this path to minimize their cost of ownership and transfer the risks of maintaining physical data centers (Berger et al., 2008).
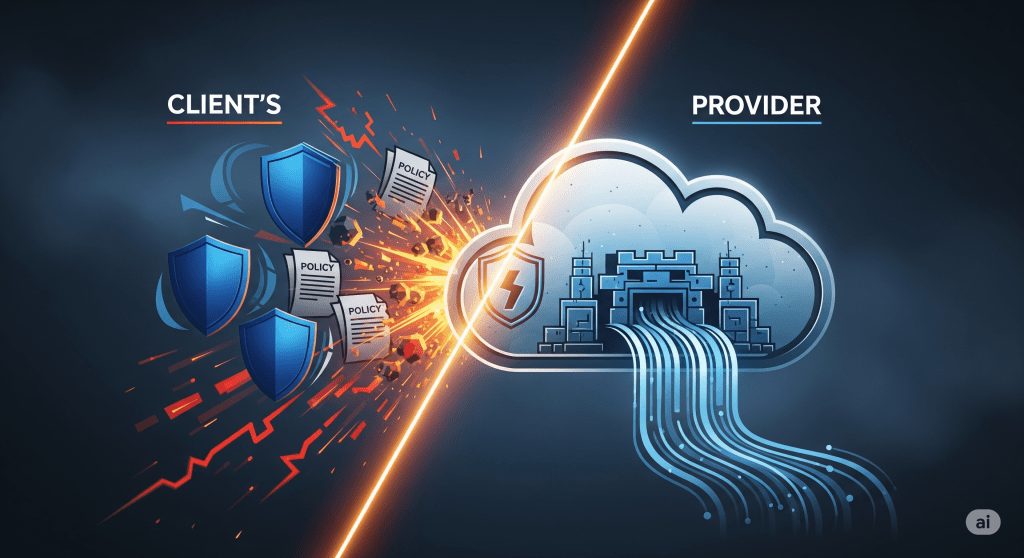
However, even the most sophisticated cloud platforms operate as companies. They are not built to accept unlimited liability for a client’s convenience. The key to successful and secure cloud operations lies in a complete understanding of the shared responsibility model. This model operates on the simple, conceptual distinction of a landlord-tenant agreement: the provider is responsible for the integrity of the building, while the client is responsible for what happens inside. The provider assumes the risk for a physical data center breach, while the client is responsible for their own software access controls and user authorization (Rao & Selvamani, 2015).
A company must implement a trusted virtual data center (TVDc) to reduce security exposure and simplify management. This is achieved by establishing trusted virtual domains and abstracting from them to enforce data isolation (Berger et al., 2008). Cloud providers, in turn, offer various models such as Platform as a Service (PaaS), Software as a Service (SaaS), or IaaS, which define where the line of responsibility is drawn. The client has the option to choose between managing a service themselves, such as a virtual server for a database, or using a pre-configured, managed service that offloads many security update responsibilities to the provider.
The Imperative of Standards and Policies
A firm’s commitment to security is best demonstrated through its adoption of rigorous standards. Given the complexity of modern business, from virtual teams to distributed IoT devices, a suite of standards is not merely a suggestion—it is a mandate. Having a framework such as ISO 27001, 27017, 27032, and NIST CSF is an excellent starting point (Tissir et al., 2021). These standards are the essential tools to uphold the expectations implied and instituted by a firm’s policies.
The implementation of these policies becomes even more critical when a company establishes its big data analytics capabilities. To effectively manage this, a company must classify its assets according to their tangibility, intangibility, and the human resources with big data-related skills (Mikalef et al., 2020). By doing so, a firm can conceptually determine the overarching impact of a successful big data analytics adoption, which extends to fiscal and market benefits. Conversely, a failure to adhere to these standards can expose the firm to significant risk.
Ultimately, these standards and policies are the tools that prevent a company from inadvertently accepting the risks of its own negligence and misconfigurations. They are a company’s internal safeguard against the perils of a complex technological ecosystem.
Disaster Recovery: A Prudent Selection
A company’s commitment to standards and policies must extend to preparing for the inevitable: business disruptions. The best method to ensure a high level of availability is dependent on a company’s use-case, but a prudent selection often involves a warm-standby disaster recovery strategy. This active/passive approach keeps a set of resources with periodic backups until a business interruption occurs. When a disaster hits, the passive resources are activated, and the replicated data ensures an optimal Recovery Time Objective (RTO) and Recovery Point Objective (RPO).
Accounting for a disruption’s financial impact requires a Business Impact Analysis (BIA). This analysis is the foundation of a proactive strategy to minimize the long-term effects of any interruption (MacNeil, 2022). A BIA identifies critical processes and resources, quantifies the impact of disruptions, and defines both the RTO and the RPO (Gartner, Inc, 2023).
This analysis provides the foundation for a business continuity plan, which discusses prevention and response strategies to keep business operations running as smoothly as possible. The establishment of a business continuity plan is guided by standards such as ISO 22301 and ISO 22313, ensuring a disciplined and comprehensive approach (Weller, 2021). Thus, a company’s readiness for cloud disasters is not a matter of luck but of strategic foresight, guided by standards and fortified by a clear understanding of its own business continuity.
References
Berger, S., Cáceres, R., Pendarakis, D., Sailer, R., Valdez, E., Perez, R., Schildhauer, W., & Srinivasan, D. (2008). TVDc: Managing security in the trusted virtual datacenter. ACM SIGOPS Operating Systems Review, 42(1), 40–47. https://doi.org/10.1145/1341312.1341321
Gartner, Inc. (2023). Definition of Business Impact Analysis (BIA)—Gartner Information Technology Glossary. Gartner. https://www.gartner.com/en/information-technology/glossary/bia-business-impact-analysis
Kirubakaran, S. (2020). Study of security mechanisms to create a secure cloud in a virtual environment with the support of cloud service providers. Journal of Trends in Computer Science and Smart Technology, 2, 148–154. https://doi.org/10.36548/jtcsst.2020.3.004
MacNeil, C. (2022, December 8). Business Impact Analysis (BIA): Prepare for Anything [2023]. Asana. https://asana.com/resources/business-impact-analysis
Rao, R. V., & Selvamani, K. (2015). Data Security Challenges and Its Solutions in Cloud Computing. Procedia Computer Science, 48, 204–209. https://doi.org/10.1016/j.procs.2015.04.171
Tissir, N., El Kafhali, S., & Aboutabit, N. (2021). Cybersecurity management in cloud computing: Semantic literature review and conceptual framework proposal. Journal of Reliable Intelligent Environments. https://doi.org/10.1007/s40860-020-00115-0
Weller, J. (2021, August 17). Business Impact Analysis Toolkit. Smartsheet. https://www.smartsheet.com/business-impact-analysis

Leave a comment